Deep Links & WebViews Exploitations Part II
- Published on
Post Date
- Authors

- Name
- Juan Urbano Stordeur
- X
- @juanurss
- Authors

- Name
- Juan Martinez Blanco
- X
- @juan-martinez-blanco

TL;DR: This post is the second of a two-part series covering Deep Links & WebViews Exploitations. This article focuses on Deep Links. It analyzes the implementation and security risks of Deep Links in Android apps, including Loading URLs in WebViews vulnerabilities and File Access Through WebViews. Deep Links & WebViews Exploitations Part I
TL;DR2: The post uses practical examples and screenshots to demonstrate these concepts, aiming to educate on potential exploits and necessary precautions. For all the practical examples and exercises of this post, we are going to use the WebViews_&_DeepLinks-true.apk application by Just Mobile Security. Additionally we’ll provide WebViews_&_DeepLinks-false.apk which mitigates the vulnerabilities analyzed in this post.
In this first article, we will specifically focus on:
- Open Redirect via Deep Link
- File Theft
Each topic in this article will be explored in detail to provide a clear understanding of their impact and mitigation strategies.
Introduction to Deep Link Security in Android Apps
This post focuses on finding, exploiting, and understanding some common vulnerabilities in Android Deep Links. Essential to this analysis are two key concepts: Static and Dynamic Analysis of Android Apps.
Static analysis involves examining the app's code to pinpoint potential weaknesses, we can achieve this by using the Nuclei tool and the Android templates provided.
Dynamic analysis, meanwhile, is about observing the app in action, particularly useful for understanding how it handles network traffic and the application's behavior, in this case we can use Frida to perform this action.
Together, these approaches provide a comprehensive analysis of the application for identifying and exploiting Deep Links vulnerabilities.
Deep Links
Deep Links are URLs designed to open directly inside a mobile app, guiding users to specific content or actions without passing through the app's home screen. They make it easier for users to access particular sections of an app from external links found in websites, emails, or other apps, improving the user experience by providing a direct path to what they're looking for. This functionality not only enhances engagement by simplifying navigation but also supports seamless integration between the app and external sources, making the app more accessible and user-friendly.
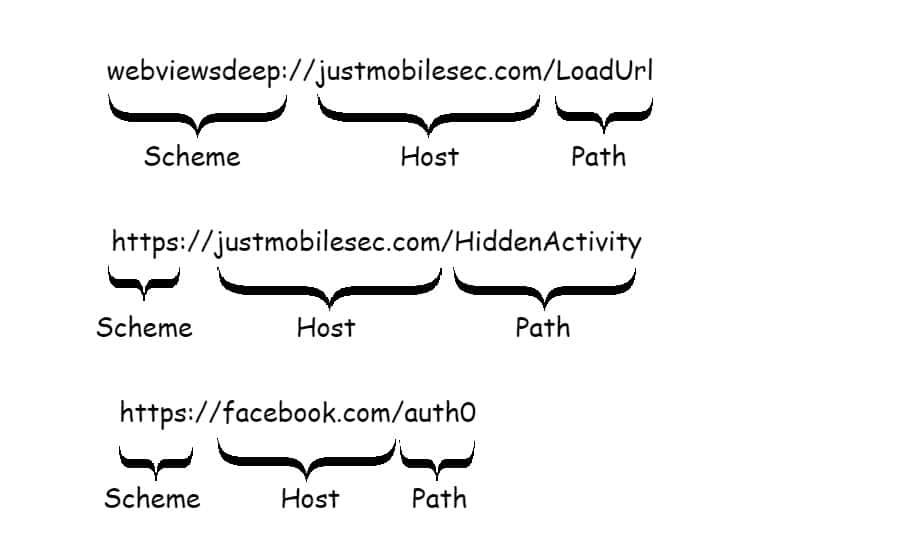
Deep Links are composed of three parts:
- Scheme
- Host
- Path
Detecting Deep Links
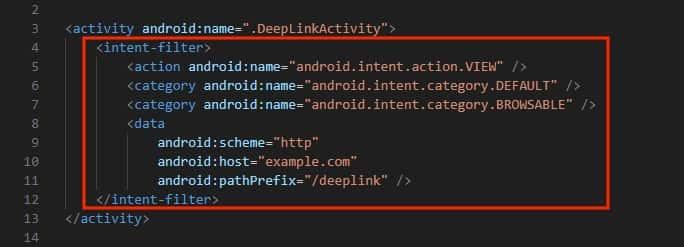
To Identify a Deep Link in an Android Application, we can look for an intent-filter declared within the AndroidManifest.xml file.
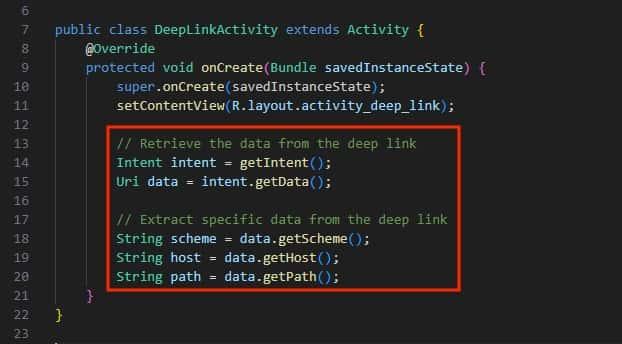
We can analyze the data passed through the intent to the Deep Link, by looking at the java implementation of getIntent().
Detecting Deep Links Statically
Using Nuclei to statically detect Deep Links, in this case using the deep-link-detect.yaml template by Hardik-Solanki. If not, you can look for the Android Manifest declaration manually, but Nuclei is really useful and easy to automate your scripts.
$ echo < Decompiled APK folder > | nuclei -t deep-link-detect.yam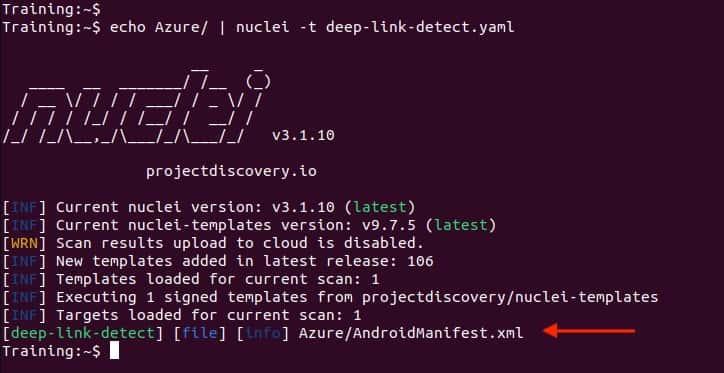
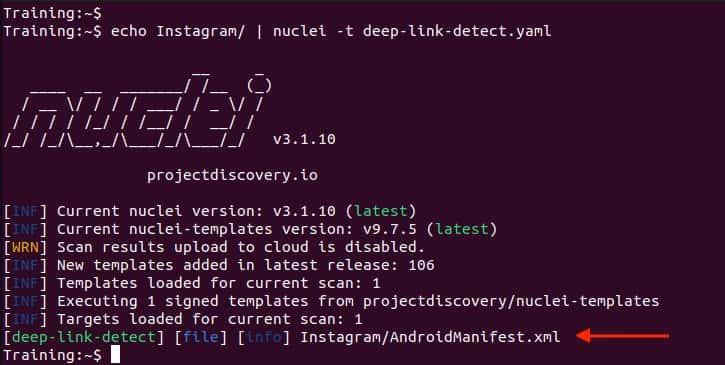
Detecting Deep Links Dynamically
Using Frida to detect Deep Links with leolashkevych’s script
$ frida -U --codeshare leolashkevych/android-deep-link-observer -f com.just.mobile.sec.webviewsdeeplinks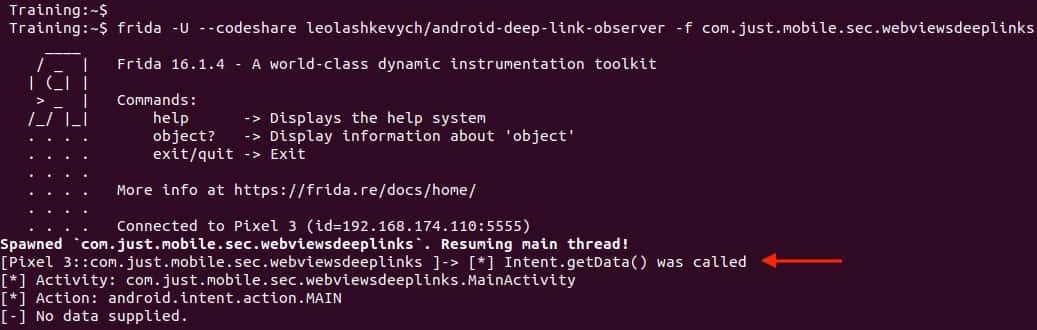
Common Vulnerabilities
Deep Links if they are not implemented correctly can introduce multiple risks especially when they are combined with the use of WebViews, if they are not configured safely. These vulnerabilities include Open Redirect Exploitation via Deep Link and potential file theft.
For penetration testers, a key strategy is to analyze controllable data and input fields within mobile applications. Determining if these inputs are sanitized is crucial. This approach helps uncover implementations in Android apps that are potentially vulnerable.
Potentially Vulnerable Functions
This article addresses a range of functions in WebViews when implemented across with Deep Links that could potentially be exploited. While we will discuss several critical ones, it's important to understand that there are many others. Each function, depending on its implementation and usage, can present unique security challenges.
1. Loading URLs in WebViews
Loading URLs into WebViews using the loadUrl() method is essential for displaying web content within a WebView. However, failing to properly sanitize and validate the inputs to this function can lead to several security risks. For instance, unsanitized inputs may allow the loading of malicious URLs. If the target loaded is susceptible to Man-in-the-Middle (MitM) attacks, for example using unencrypted communications, the WebView could be forced to display fake websites, deceiving users into disclosing sensitive information. Moreover, loading content from untrusted sources without proper validation can permit the execution of harmful scripts, especially if settings such as setJavaScriptEnabled(true) are activated.
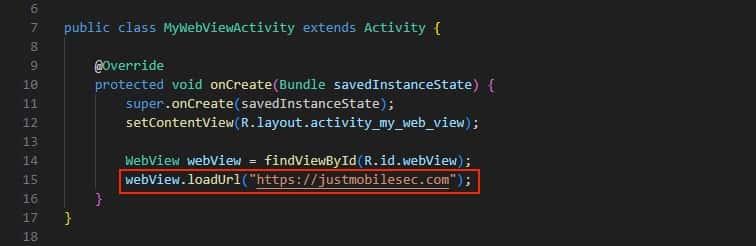
This function is commonly used along with deep links to load specific web content within the web view which enlarges the attack surface and exposes the application to potential exploitation via deep link.
There are many ways to implement the loadUrl() method that could give us hints of proper or improper sanitization of the input
javascript loadUrl("javascript:" + str);loadUrl(String.format("file:///%s", new Object[]{brVar.d()}));loadUrl("about:blank");loadUrl("file:///android_asset/index.html");
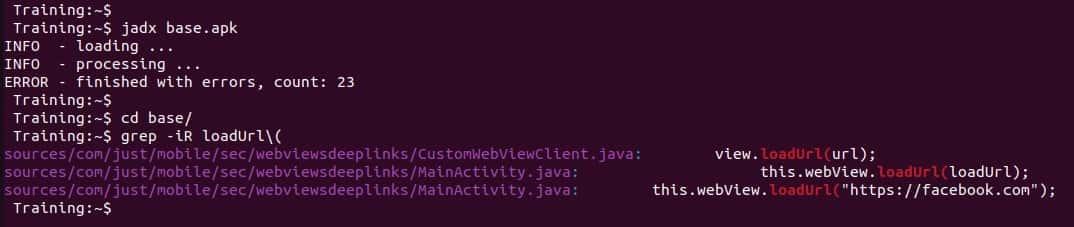
A quick approach to find these implementations is to decompile the apk using apktool or jadx and grep the function
$ grep -iR loadUrl\(Another approach is like we did before using nuclei to find the implementation.
Open Redirect Exploitation via Deep Link
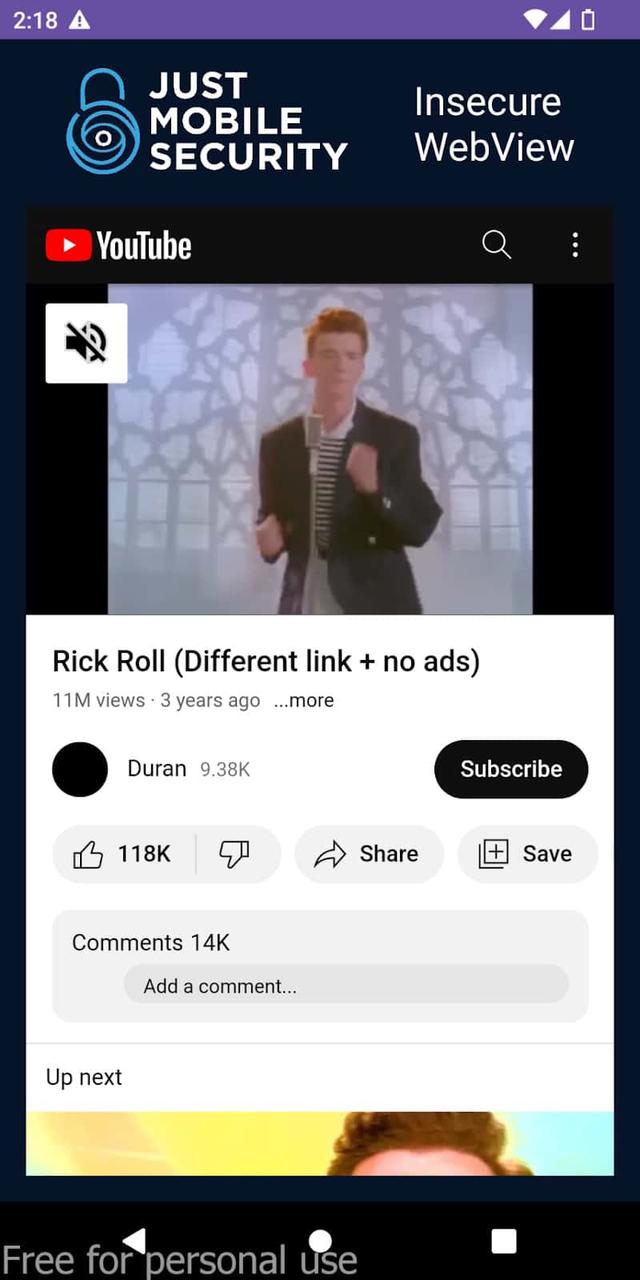
To be able to exploit an open redirect we need to find the vulnerable input where WebView interacts with the Deeplink, in the following steps we will search for it and interact with the Deeplink using ADB and injecting an arbitrary URL, in this case, a RickRoll Youtube link.
For this demonstration, we will keep using the WebViews_&_DeepLinks App and we are also going to use JADX to decompile the JAVA code and analyze it to find the vulnerable implementation.
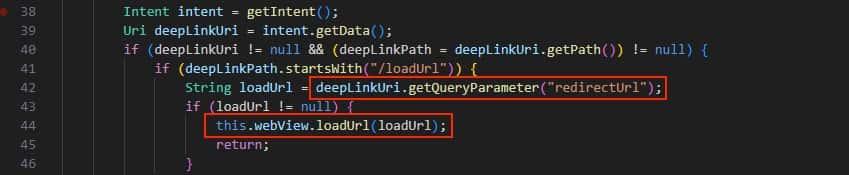
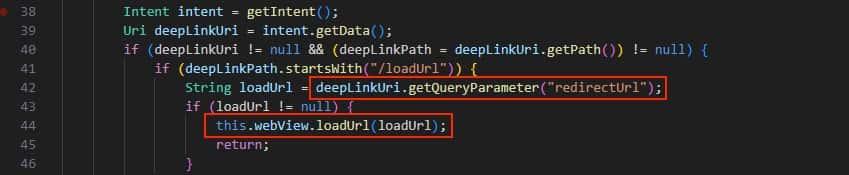
- We analyze the JADX decompiled code and find the WebView loadUrl() function.
- Here we notice the redirectUrl parameter that is being used to redirect the user without any sanitization.
- We can also notice that the data is coming from a Deep Link.
- We are going to test this Open Redirect using ADB
$ adb shell am start -a android.intent.action.VIEW -d "webviewsdeep://justmobilesec.com/loadUrl?redirectUrl=https://youtu.be/xvFZjo5PgG0?feature=shared"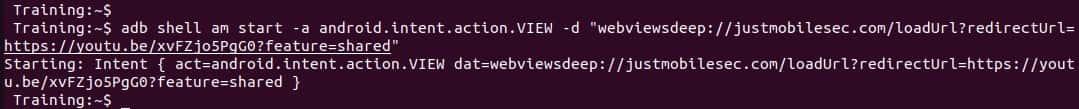
The exploitation of the Open Redirect will be possible due to the unvalidated loadUrl() function.
2. File Access Through WebViews
The setAllowFileAccess() function in WebViews allows JavaScript to access local files and content from any origin, removing the same-origin policy restrictions. This enables interactions with resources across different origins, facilitating otherwise restricted web requests. However, this functionality also poses risks, such as cross-origin attacks, data exposure, and potential file theft, by bypassing important security measures. It can lead to malicious code execution and UI manipulation, compromising app security.
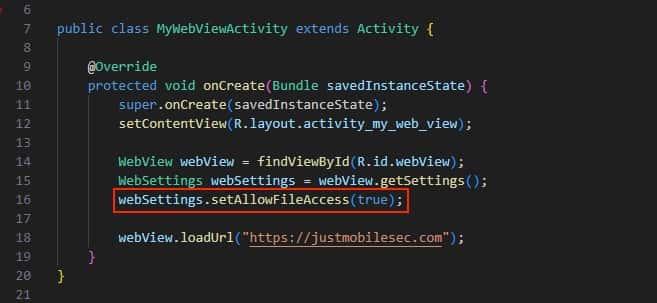
File Theft in WebViews
If the call to the loadUrl() function would be correctly sanitized and validated for example only loading URLs from trusted domains the exploitation attempt would have failed.
We are going to use JADX to decompile the WebViews_&_DeepLinks App JAVA code and analyze it to find the vulnerable implementation.
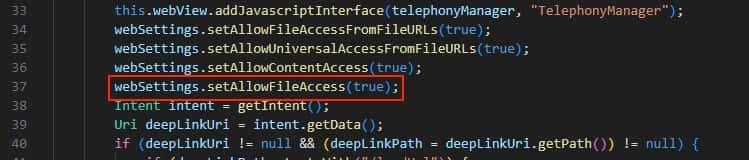
- We analyze the JADX decompiled code and find the WebView setAllowFileAccess(true) declaration.
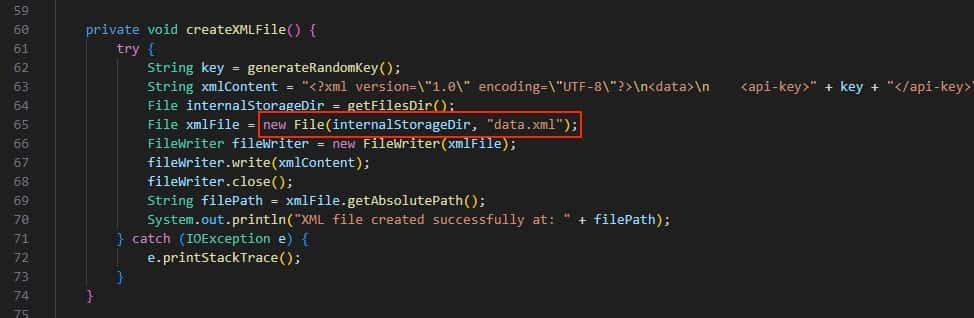
- Analyzing the rest of the application’s code we notice an xml file created and stored in the internal storage.
- Using the loadUrl() method via Deep Link we will access the file.
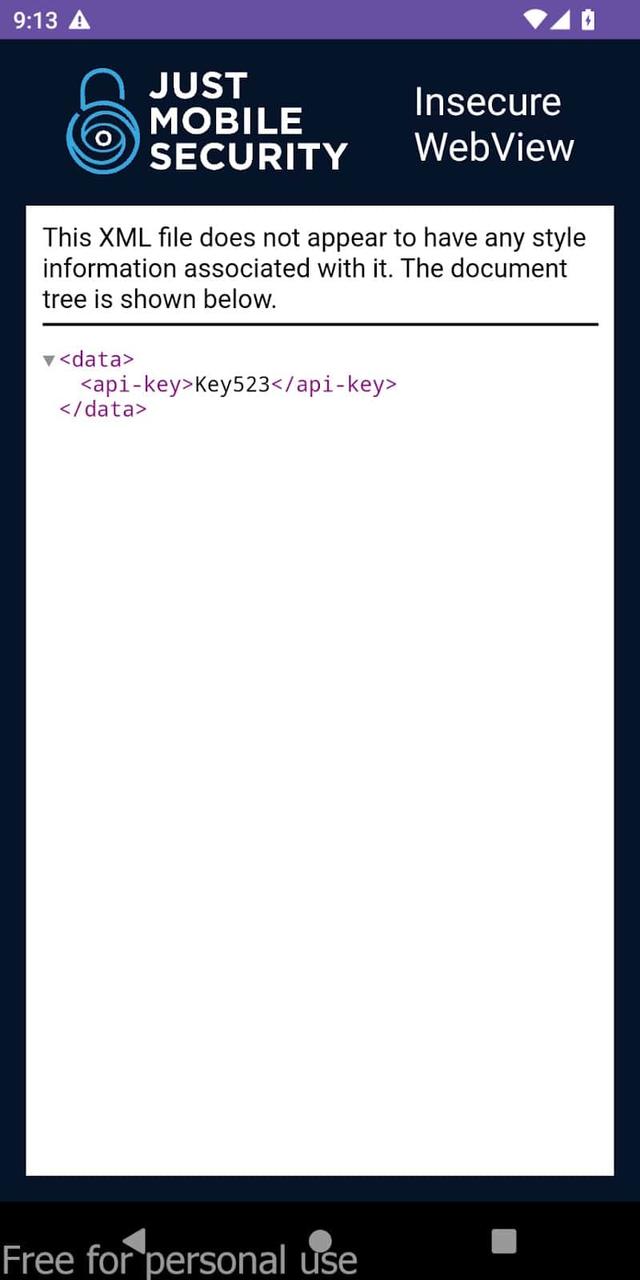
$ adb shell am start -a android.intent.action.VIEW -d "webviewsdeep://justmobilesec.com/loadUrl?redirectUrl=file:///data/data/com.just.mobile.sec.webviewsdeeplinks/files/data.xml"
File can be accessed due to the insecure setting setAllowFileAccess(true) implemented in the application code.
In conclusion, understanding WebView & Deeplinks vulnerabilities in Android applications is crucial for app security. This post has highlighted key areas like Loading URLs in WebViews and File Access through WebViews, illustrating how these features could be exploited.
There are many ways of exploiting these vulnerabilities and the examples were demonstrative to explain them. Remember, while these technologies offer numerous benefits, their secure implementation is vital to protect both the app and user data.